Your first line of defense begins with a cyber vigilant workforce
Employees are the easiest entry point for hackers. With simple tricks, compromising one is enough - that's why 80% of attacks target them. While specilists monitor threats, the rest of your workforce stays disengaged. Hackers exploit this gap, leaving your business exposed!
Learn moreAll it takes is ..
1 person
1 click!
Regardless of how cautious or careless an employee may be, hackers have strategies to exploit all three key areas of vulnerability:
- Knowledge Gaps
- Psychological Triggers
- Behavioral Patterns

Turn Awareness into Vigilance
Awareness is knowing the risks; vigilance is acting to prevent them. Its time to move employees beyond understanding threats and start anticipating them.
Aquta Human Firewall Workshops
The Human Firewall Workshop transforms employees into Cyber Vigilantes, fully engaging them with hands-on training using the Vigilante Threat Monitoring Dashboard.
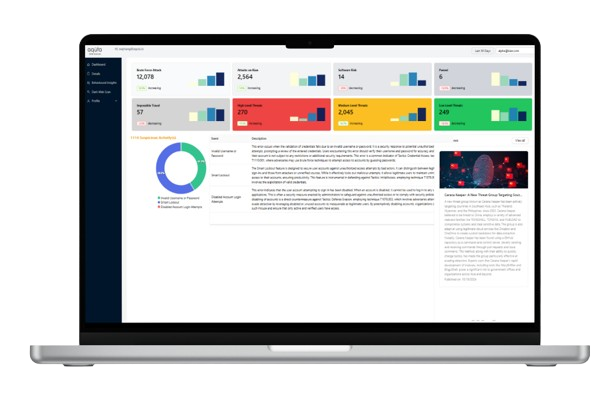
Aguta Vigilante Monitoring Tool For Employees
Vigilante is an automated solution that protects your organization's Office 365 attack surfaces with real-time threat visualization. Its user-friendly dashboad simplies monitoring for non-IT employees, empowering them to be your human firewall.
Use experience
"I never knew how vulnerable I was to cyber criminals until I attended the Aquta Human Firewall Workshop.
Now, I have stopped
using public wifi's!"
"We had painful ransomware attack which was totally avoidable. Aquta Vigilante would have alerted the vulnerability immediately and saved us the pain and cost!"
Find a plan to suit your team
Basic
Aquta Vigilante Human Firewall
Monitoring Platform for Employees
(suitable for MS365 users only)
Premium
Aquta Vigilante Human Firewall
Full Program for Employees
(suitable for MS365 users only)
Stay updated about all the cyber news

Test Teast New CRON#TRAP Malware Infects Windows
A newly discovered malware, named CRON#TRAP, is now infecting Windows computers by deploying a hidden Linux virtual machine...
Read all
Actively Exploited CVE-2024-43093 Vulnerability
Google has warned of a security flaw in its Android operating system, CVE-2024-43093, which is currently being exploited in real-world ...
Read all
Hackers Exploit Roundcube Webmail XSS
Unknown attackers have been trying to exploit a fixed security issue in the open-source Roundcube webmail software to steal…
Read allKeep the crims out today!
Try for free now.
